Scattered LAPSUS$ Hunters: The Unmasking of ‘Rey’ and the Rise of ShinySp1d3r
The cybercrime landscape shifted dramatically this week with the revelation of the identity behind “Rey,” the prominent figure leading the Scattered LAPSUS$ Hunters (SLSH) hacking group. For months, SLSH has dominated headlines through aggressive data theft and extortion tactics targeting major corporations. Now, after relentless tracking by security researchers and a direct appeal to his family, Rey has agreed to discuss his involvement, offering a rare glimpse into the inner workings of this prolific criminal enterprise.
SLSH isn’t a singular entity, but rather a convergence of three notorious hacking groups: Scattered Spider, LAPSUS$, and ShinyHunters. These groups operate within a sprawling network of Telegram and Discord servers, collectively known as “The Com,” a largely English-speaking cybercriminal community.
The Salesforce Attacks and Insider Threat
In May 2025, SLSH launched a sophisticated social engineering campaign targeting Salesforce users. Utilizing voice phishing, they tricked employees into connecting malicious applications to their organizations’ Salesforce portals. This breach led to the theft of data from dozens of companies, including industry giants like Toyota, FedEx, Disney/Hulu, and UPS. The stolen data was then threatened for publication on a dedicated leak site unless substantial ransoms were paid.
More recently, SLSH has actively sought to recruit “insiders” – disgruntled employees with access to internal networks – offering a share of the ransom payments in exchange for privileged access. This tactic, coupled with a recent incident at Crowdstrike where an employee was terminated for allegedly sharing internal screenshots with the group (TechCrunch), highlights the growing threat of internal compromise.
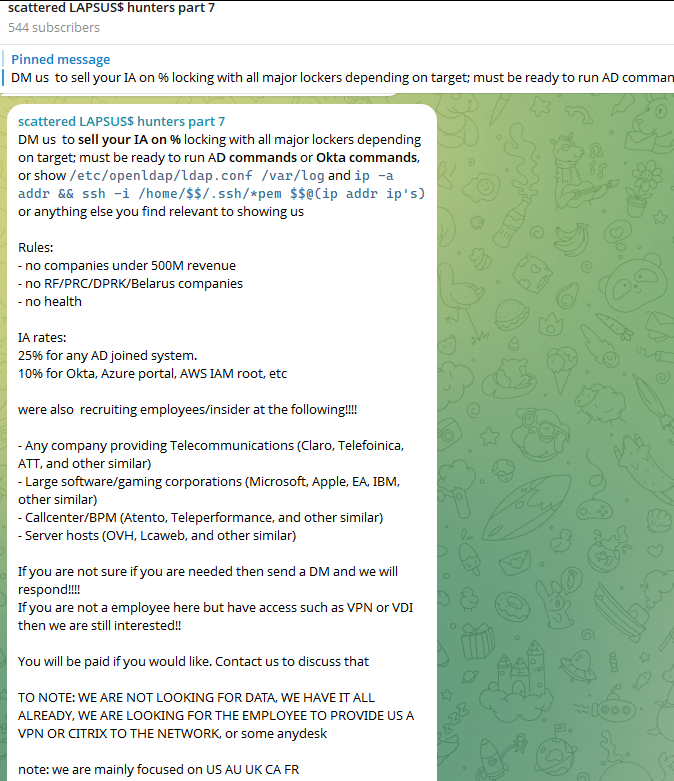
From Ransomware Affiliate to Operator: The Birth of ShinySp1d3r
Historically, SLSH members have leveraged existing ransomware tools from affiliate programs like ALPHV/BlackCat, Qilin, RansomHub, and DragonForce. However, the group recently announced the launch of its own ransomware-as-a-service (RaaS) operation, dubbed ShinySp1d3r. This marks a significant escalation in their capabilities and ambition.
The driving force behind ShinySp1d3r is “Rey,” a core SLSH member and one of the three administrators of the group’s Telegram channel. Prior to this, Rey held administrative roles within other prominent ransomware operations, including Hellcat, which targeted companies like Schneider Electric, Telefonica, and Orange Romania.
Rey’s digital footprint extends to the notorious BreachForums, where he served as an administrator for multiple iterations of the forum, even publicly acknowledging FBI seizures of the platform (FBI Announcement). The FBI has consistently described BreachForums as a central hub for cybercriminals involved in data trafficking and extortion.
Unraveling Rey’s Identity: A Trail of Digital Breadcrumbs
The path to identifying Rey began with a series of operational security (OpSec) failures. Intel 471 identified Rey as an active user on BreachForums, posting over 200 times between February 2024 and July 2025, initially under the handle “Hikki-Chan.” His first post on the forum involved sharing data allegedly stolen from the U.S. Centers for Disease Control and Prevention (CDC).
A crucial slip-up occurred in May 2024 when, using the Telegram username @wristmug, Rey posted a screenshot of an automated sextortion scam email he’d received. In a moment of apparent carelessness, he redacted the username portion of the email address but left his password and ProtonMail domain (@proton.me) visible.
From Online Persona to Real-World Location
This seemingly minor oversight proved pivotal. Searching the unique 15-character password in the breach tracking service Spycloud revealed a single associated email address: [email protected]. Spycloud data indicated the credentials had been compromised twice in early 2024 through an infostealer Trojan. Further investigation by Intel 471 linked [email protected] to a BreachForums user named o5tdev.
Online searches revealed o5tdev’s involvement in website defacements, specifically with a group called Cyb3r Drag0nz Team, known for DDoS attacks, data leaks, and hacktivism. SentinelOne reported that Cyb3r Drag0nz Team claimed responsibility for leaking data on over a million Israeli citizens. Flashpoint identified o5tdev as active on Telegram in 2023 and early 2024, posting in Arabic on anti-Israel channels.
The Ginty Connection and the Amman Lead
Rey’s Telegram account (ID7047194296) was highly active in a cybercrime-focused channel called Jacuzzi, where he revealed his father was an airline pilot and claimed Irish heritage, even sharing a graphic illustrating the prevalence of the surname “Ginty.” Spycloud data linked Rey’s computer to a shared Microsoft Windows device in Amman, Jordan, with multiple users sharing the last name Khader.
Infostealer data recovered from the device revealed an entry for Zaid Khader, age 46, whose mother’s maiden name was Ginty. The data also showed frequent access to internal websites for Royal Jordanian Airlines. This led investigators to identify Rey’s full name as Saif Al-Din Khader.
A Confession and a Plea
Unable to contact Saif directly, investigators reached out to his father, Zaid. Saif, anticipating his father’s skepticism, contacted KrebsOnSecurity directly, confirming his identity and acknowledging his involvement with SLSH. He claimed to be attempting to extricate himself from the group and expressed concern that publicity could jeopardize potential cooperation with law enforcement.
Saif revealed that ShinySp1d3r is essentially a modified version of the Hellcat ransomware, enhanced with AI tools. He also stated he had contacted Operation Endgame, a law enforcement initiative targeting cybercrime services, seeking assistance.
While claiming cooperation with authorities, Saif remained hesitant to provide specific details, fearing repercussions. He expressed a desire to move on from his involvement, even if it meant facing imprisonment.
What does this unmasking mean for the future of Scattered LAPSUS$ Hunters? And what steps can organizations take to better protect themselves against insider threats and sophisticated ransomware attacks?
Frequently Asked Questions About Scattered LAPSUS$ Hunters
What is the primary goal of the Scattered LAPSUS$ Hunters group?
The primary goal of SLSH is financial gain through data theft and extortion. They target organizations and demand ransom payments to prevent the public release of sensitive information.
How does the Scattered LAPSUS$ Hunters group recruit new members?
SLSH actively recruits “insiders” – employees with access to internal networks – offering a share of the ransom payments in exchange for privileged access. They also leverage existing cybercriminal communities to find skilled individuals.
What is ShinySp1d3r and how does it differ from other ransomware?
ShinySp1d3r is SLSH’s own ransomware-as-a-service (RaaS) operation. It’s based on the Hellcat ransomware but enhanced with AI tools, giving them greater control and potential for customization.
What role did operational security (OpSec) failures play in identifying ‘Rey’?
Rey’s identity was revealed through a series of OpSec mistakes, including leaving a password visible in a screenshot and sharing personal details on Telegram, which allowed investigators to connect his online personas to his real-world identity.
What is Operation Endgame and how is it related to the SLSH investigation?
Operation Endgame is an ongoing law enforcement initiative targeting cybercrime services, vendors, and their customers. Saif Al-Din Khader claims to have contacted Operation Endgame seeking assistance in extricating himself from SLSH.
Share this article to help raise awareness about the evolving threat landscape and the importance of cybersecurity vigilance. Join the discussion in the comments below – what further steps should be taken to combat groups like Scattered LAPSUS$ Hunters?
Disclaimer: This article provides information for educational purposes only and should not be considered legal or financial advice.
Discover more from Archyworldys
Subscribe to get the latest posts sent to your email.

